Security by Design: Building Confidence in DevOps for Regulated Industries
In highly regulated industries like banking, insurance, or healthcare, adopting DevOps is not as simple as “moving fast and breaking things.” The reality is quite the opposite: move carefully, document everything, and remember that failures may have regulatory consequences. In such environments, a single failure can translate into a potential compliance violation — and therefore, DevOps must evolve into DevSecOps, where security and compliance are embedded into every step of the development lifecycle.
Balancing Speed and Accountability
DevOps promises speed, agility, and automation. But in regulated industries, these benefits must coexist with rigorous demands for compliance, auditability, and risk control. Every deployment, change, and log must be traceable. Every process must align with internal governance and external regulations. The challenge is clear: how can organizations enjoy the efficiency and innovation DevOps offers without compromising on the strict compliance standards that govern their industry?
Balancing Speed and Accountability
DevOps promises speed, agility, and automation. But in regulated industries, these benefits must coexist with rigorous demands for compliance, auditability, and risk control. Every deployment, change, and log must be traceable. Every process must align with internal governance and external regulations. The challenge is clear: how can organizations enjoy the efficiency and innovation DevOps offers without compromising on the strict compliance standards that govern their industry?
The Ownership Dilemma: “You Build It, You Run It”
One of the guiding principles of DevOps is “You build it, you run it.” It emphasizes accountability and end-to-end ownership for development teams. However, for developers in regulated industries, this principle often raises concerns. In traditional environments — particularly in banks — responsibilities have long been clearly separated. Developers built the software; operations teams ran it; compliance officers ensured it met regulations. Everyone knew their boundaries. With DevOps, those boundaries blur. Developers suddenly find themselves accountable not just for functionality and performance, but potentially for regulatory compliance and operational security as well. This can feel like a liability transfer — and understandably, it can lead to resistance and anxiety.
Our Approach: Building a Developer Security Landscape
To address these concerns, our focus has been on creating what we call a Developer Security Landscape — an environment where developers can see and understand the protections surrounding their work. In earlier stages, we implemented a range of security features and presented them to developers. But we soon realized that simply telling teams “you’re protected” wasn’t enough. The protections needed to be visible, transparent, and integrated into their daily tools. Our next step, therefore, was to make these security mechanisms tangible. By providing architecture diagrams and visual interfaces that show exactly where and how protection occurs — from data encryption to access control to monitoring — developers gain clarity.
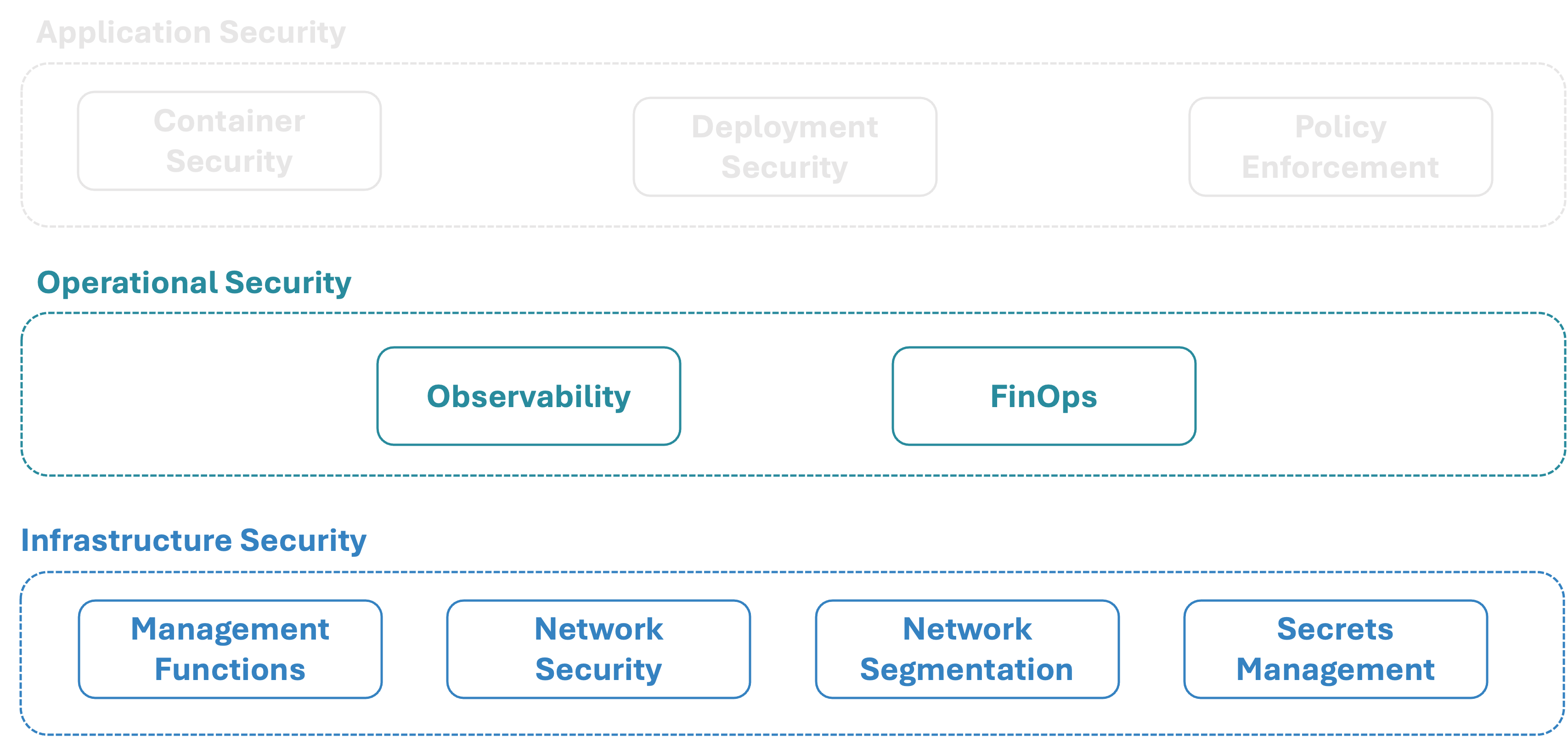
Hypothesis: Visibility Builds Confidence
Our hypothesis is straightforward: When developers can see exactly where and how they’re protected, anxiety and resistance transform into confidence. This is more than a cultural shift — it’s a psychological one. By making safety nets visible rather than merely functional, we reduce uncertainty and help developers feel supported rather than burdened by compliance requirements.
Security by Design: The Way Forward
“Security by design” is not just about embedding security in code; it’s about embedding trust in the development process. In regulated industries, this means designing systems, workflows, and cultures where developers can move forward confidently — knowing that compliance and safety are integral parts of their daily environment, not external constraints. In the end, DevSecOps in regulated sectors is not about choosing between speed and compliance. It’s about designing for both from the start — and ensuring that security is not just enforced, but experienced.
